Tamper Evident Seals - Part II
•
Christian Reitter
In part II of this article series, I show some practical examples of opening tamper evident seals without detection.
Contents
Consulting
I’m a freelance Security Consultant and currently available for new projects. If you are looking for assistance to secure your projects or organization, contact me.
Strategy: Opening the Seal
Attack Concept
Sticker-based seals can be applied to different surfaces and are compatible with many different package designs. However, their reliance on adhesives is also a fundamental weak spot. Once an attacker is able to sufficiently weaken the adhesive without visibly damaging the surface of the seal or of the protected package, there is a chance that the seal can be removed with very little separation force. This defeats the tamper detection properties by keeping the fragile lower security layer intact instead of ripping it off as expected.
There are multiple practical methods to do accomplish this, for example by applying heat or using various solvents.
My personal preference is to apply isopropanol and use a blade to gently pry the sticker loose, allowing more solvent to flow under it. Some patience is required while repeating this procedure, but it was often sufficient to remove the seal with little or no damage.
For some package surfaces such as absorbent cardboard, there can be some remaining residue on the package, but I assume that there are ways to hide or avoid that as well. I have not focused on this aspect during my experiments.
Note that to a large extent, the weaknesses of this type of tamper evident seal are not really news in the security researcher community. For example, the wallet.fail presentation at 35C3 has brought up this problem in the context of hardware wallet security back in 2018. Still, I think it is interesting to explore this topic a bit more and show some additional examples of devices “in the wild”.
Breaking Simple Designs
Let’s begin with some simple seals with a monochrome background:

As you can see from the next image, patience and luck do play a role here. The right half of the seal came off intact while the left half has some defects. To highlight the open state of the seal, I applied two bright marker strips under it. Note that the orange color is visible through the semi-transparent areas where the seal has been damaged. The contrast change in these regions is the main way to visually detect the tampering.

I think it is plausible that defects in simple backgrounds are easier to mask with a new background layer of suitable color or some partially applied paint. Although I have not looked into the topic of re-making seals in a regular laser printer, copies of this kind of black-on-white sticker can probably be printed at home, particularly if the targeted recipient of the package is not aware of what the original sticker looks like up close. For products sold to regular customers, there usually is no “known good” unit from a previous shipment to compare to.
The following seal was located on the inner package of a recent Lenovo business laptop. It only has small reflective icons and otherwise simple backgrounds. My impression is that this seal was designed primarily to spot opened laptop packages during refunds as discussed in article part I and less as a strong protection against supply chain attacks during shipping.

Breaking Holographic Designs
Many security stickers have a multi-colored reflective design or hologram components. Although one can attribute some minor security benefits to this as discussed in a later section, the psychology of an eye-catching and visually sophisticated stickers definitely plays a role as well.
Orange tape is again used to highlight accessible areas after lifting the seal:

As you can see, it would be difficult to determine that this package has been opened based on the visual state of the seal:
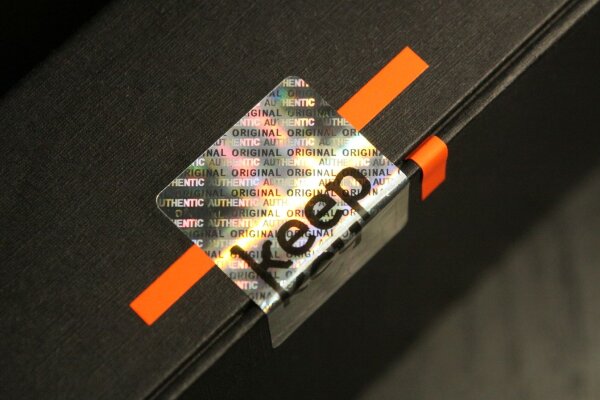
Unfortunately, this is also relevant for the Trezor models:


Here is another lifted seal on the BC Vault:
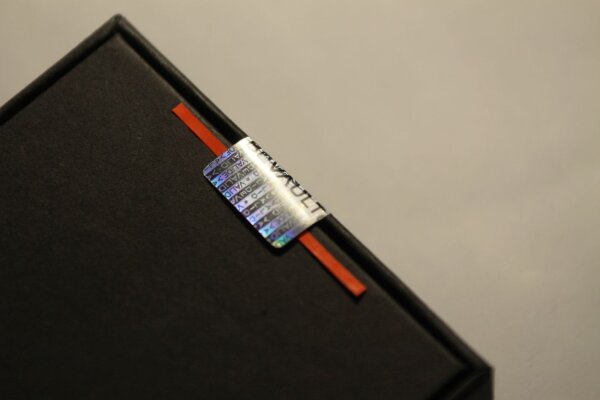
If you look closely at the left border of the image, you can see some slight color difference in the black cardboard surface of the package. This is one of the - probably avoidable - side effects of the solvent used in this attack method.
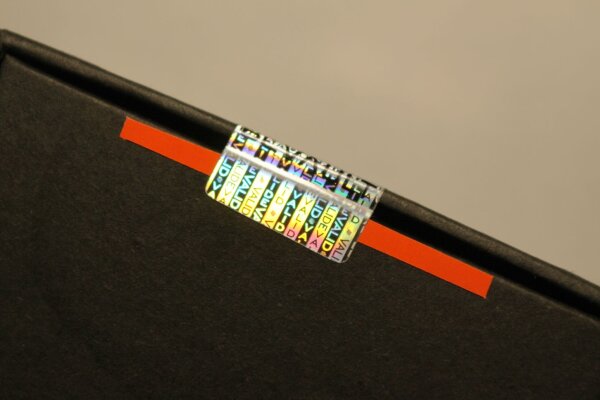
Hiding Seal Defects
The seal variants presented so far do not have any built-in unique property that can be identified by the customer. Generic seals make a successful attack easier since they are interchangeable. For example, an attacker can lift an identical seal off a second package without any defects beforehand and keep it ready to apply it to the tampered package. With unique labels, it is much more difficult to re-use seals that were meant for other packages, for example units stolen from the original factory.
Due to this, I was interested in some of the properties of the seal on the YubiHSM2 device since it has a unique serial number. This number is present both in regular writing as well as an encoded QR code. Is this resistant to the known attacks?
During the first seal removal, I did not use enough solvent and time to properly dissolve the glue under the seal. This resulted in a damaged area when peeling it off, correctly indicating the tampering. Although it is not quite as visible in the provided static photograph, this section shows some characters of the word “VOID” where the reflective layer has ripped off and the seal has become transparent.
The damaged area is 3mm x 15mm in size and definitely noticeable to a cautious customer once the package is inspected from different angles and lighting conditions:

I recently had the chance to repeat this experiment on the same type of package and seal. By using significantly more isopropanol, the glue dissolved much better and the seal came off with just one small damaged section that is 2mm x 2mm in size. It is visible as a transparent “C” next to the end of the black serial number.

I think it is plausible that with more attempts, more patience, different solvents or other techniques the seal can be taken off completely without visible damage. However, let’s assume that the attacker needs this particular seal and is not satisfied with how it came off. Is it possible to mask the damaged section and pass it off as new and untampered?
To test this, I cut a small section of the more damaged first seal and applied it under the damaged transparent area of the second. The backside of this “transplanted” patch is visible in the upper right corner of the sticker:

The end result of this simple repair was better than expected. While the complex background pattern does not match, the reflective surface still works well enough that the difference is easy to miss without using a magnifying glass:
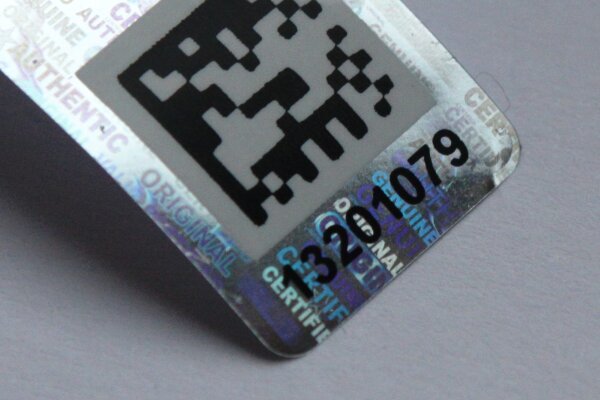
It is probably fair to say that this case of tampering would not be detected by most customers of the device.
Preliminary Conclusion
In my personal opinion, adhesive seals are only a weak line of defense against attackers that are willing to go through the other efforts involved in mounting a supply chain attack against you or your customers. This is clearly not an individual problem of low-quality seals or a single seal manufacturer. In some cases, the local protection of the seal can also be circumvented by opening other parts of the package. Consequently, there is a need for security mechanisms that do a better overall job than adhesive stickers.
However, superior commercial solutions for this are apparently hard to find, at least judging by what is used in relevant industry fields such as hardware wallets, smartcards and inexpensive HSMs. Part III of this article series will explore some of the currently published approaches and related aspects in solving this problem.