OLED Side Channel - Summary October 2019
•
Christian Reitter
ID:
CVE-2019-14353,
CVE-2019-14354,
CVE-2019-14355,
CVE-2019-14356,
CVE-2019-14357,
[...]
During security research in April 2019, I have discovered that the common OLED SSD1306-like displays used in many cryptocurrency hardware wallets and other embedded devices are leaking information about the display contents towards the USB interface from which the device is powered. This represents an interesting side channel that had so far not been discovered by other vendors and researchers.
Contents
Consulting
I’m a freelance Security Consultant and currently available for new projects. If you are looking for assistance to secure your projects or organization, contact me.
Technical background
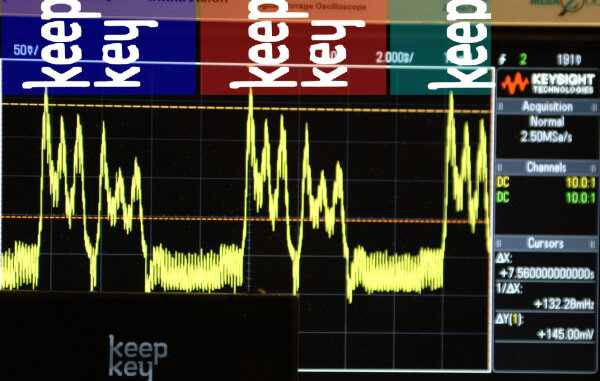
Illuminating the OLED pixels takes a comparably large amount of current per pixel and this type of display illuminates pixels on a line-by-line basis. As a result, there is a strong electrical side channel for the display contents through the current fluctuations on the USB power line that can be measured without hardware modifications to the device itself.
Here is a graphical representation of the effect on an unmodified KeepKey, traced over 2½ display cycles:
Security implications, attack scenario, mitigations
The side channel is relevant since the security design of this class of devices is built to some degree on the assumption that the display contents are readable by the user, but unreadable to other involved electronics. If this confidentiality assumption does not hold in practice, there is the possibility that malicious equipment is able to recover significant portions of PIN codes or BIP39 mnemonic words.
Many of the relevant technical aspects and implications are described in the Trezor blog article on the issue that I have co-written.
I will present more details and attack scenario considerations via additions to this post and later articles.
Practical impact
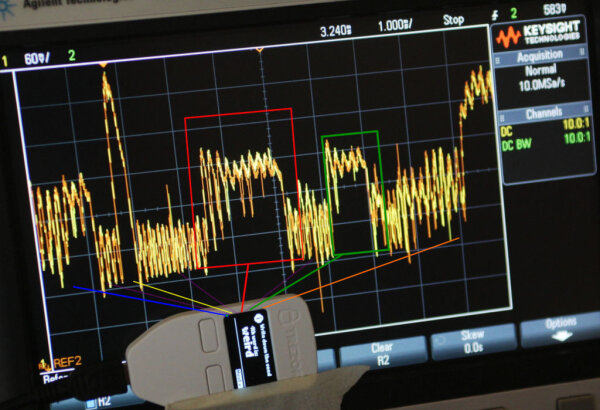
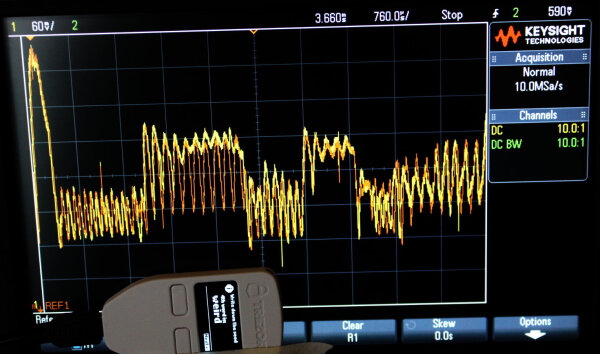
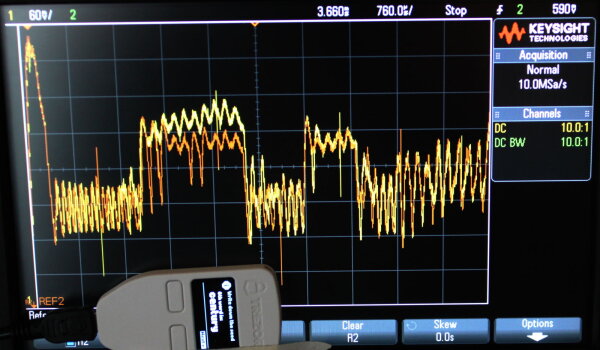
Power analysis shows this correlation on the BIP39 secret word display of the Trezor One.
weird (yellow) vs. cram (orange):
weird (yellow) vs. zoo (orange):
century (yellow) vs. cram (orange):
Disclosure Coordination
From April to August 2019, I’ve analyzed a number of devices for their susceptibility to this attack and responsibly disclosed the issue to the affected vendors. Coordinating the disclosure of a hardware vulnerability among multiple competing vendors is not a straightforward process and there were a number of challenges along the way. I may write about them at some point in the future.
CVEs
I initially requested a CVE ID from MITRE in July.
Due to CVE Numbering Authority rules, the vulnerability was split into individual CVEs on a per-vendor basis:
| CVE | product | notes | vendor reference |
|---|---|---|---|
| CVE-2019-14353 | SatoshiLabs Trezor One | article | |
| CVE-2019-14354 | Ledger Nano S, Ledger Nano X | article | |
| CVE-2019-14355 | ShapeShift KeepKey | article | |
| CVE-2019-14356 | Coldcard MK1, Coldcard MK2 | article | |
| CVE-2019-14357 | Mooltipass Mini | article | |
| CVE-2019-14358 | Archos Safe-T | - | |
| CVE-2019-14359 | REAL Security BC Vault One | minor security impact due to lack of secrets on the screen | article |
| CVE-2019-14360 | Hyundai-Pay Kasse HK-1000 | - | |
| CVE-2019-18673 | Shift Cryptosecurity BitBox02 | reference |
Other products
There are at least two additional products that may be affected in some form, but the vendors have not shown any interest in the issue.
Detailed timeline
| Date | info |
|---|---|
| 2019-04-08 | Information leak first discovered during Trezor One research |
| 2019-04-08 | Initial disclosure to SatoshiLabs |
| 2019-04-29 | Received KeepKey hardware |
| 2019-05-02 | Initial disclosure to ShapeShift (KeepKey) |
| 2019-05-04 | First communication attempt with Archos |
| 2019-05-07 | Initial disclosure to Ledger for Nano S, reference to Nano X |
| 2019-05-08 | Initial disclosure to Mooltipass |
| 2019-05-08 | Initial disclosure to Coinkite |
| 2019-05-09 | Initial disclosure to REAL Security |
| 2019-05-12 | First communication attempt with Hyundai-Pay |
| 2019-05-15 | Ledger informed of initial Nano X results |
| 2019-05-29 | Ledger requests 90 days embargo (starting from early May) |
| 2019-07-23 | CVE assignment requested |
| 2019-07-28 | CVEs assigned by MITRE |
| 2019-08-07 12:00h CEST | End of the coordinated embargo date, public disclosure |
This list is incomplete and will be extended.
Bug bounty
SatoshiLabs and Ledger have provided a bug bounty.
In 2021, ShapeShift has retroactively decided to award a bug bounty for this issue as well.
Acknowledgements
Hardware
During this research, I have received a test device from the following vendors:
- 1x Nano X from Ledger
- 1x BC Vault from REAL Security
- 1x Mooltipass from Stephan Electronics
- 1x BitBox02 from Shift Cryptosecurity
This was done mainly to speed up the analysis on devices with slow shipping or difficult availability.
Relevant hardware gifts from previous research:
- SatoshiLabs - multiple Trezor One devices
- ShapeShift - 3x KeepKey devices (part of a previous bug bounty)